so this night i'm going to show you how to do a sql injection. well you already know that i do blind sql injection in my older post but this time i'm going to do sql injection which is more easier than the blind sql injection
so i'm using two machine which is kalilinux, iso file which is from_sqli_to_shell_pg_edition_i386.iso (you can download the iso file from pentester lab just type in the google "from sql to shell")
so fireup your kalilinux and the target machine. make sure you can ping the website. so this will be the page of the target website. and let just cut to the chase i try every link to find which one is link is vulnerable to sql injection by putting single quote to some url and yea i found it was at cat.php
so there you go there is bunch list of your target web directories.
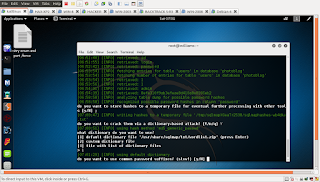
but if you want to do it manual first you have to determine by how many cplumn that are actually use u can use that with ORDER BY command so try to add some value to order by to determine how many column that they use.
so i got this error message when inserting 5 value at order by
so there is 4 column after determine the value lets figured what kind of type that they use you can test every parameter using UNION command
and after that you can also detect the version , current_user , database using union command
so we get all the necessary information lets indentify the column and table name by using this command
now for the fun part you can now retrieve admin account and password using this command
ahah! we get the admin account and password but it was hash no worries we can solve this by two way either using search engine or john the ripper
so right now i'm using search engine to encode the hash just simply copy paste the hash and wala! there you go this hashes is already been encode to some website so the password was "P4ssw0rd"
as you can see we now take control of the admin account now
have a nice day ^_^ i'm literally at the rooftop right now because the connection was bad at my flat